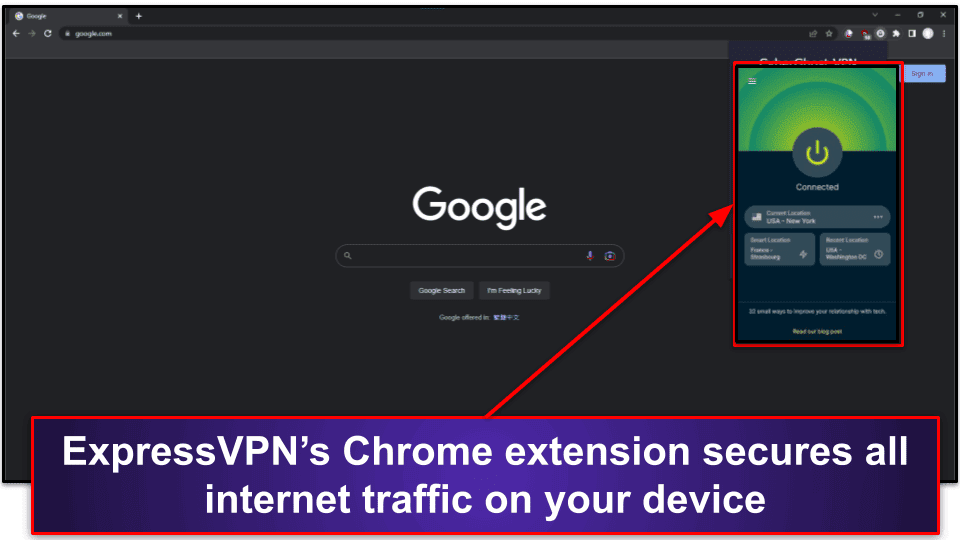
Top Free VPNs for Chromebook: Secure Browsing Without the Cost
Top Free VPNs for Chromebook: Secure Browsing Without the Cost Chromebooks, with their lightweight operating system and focus on cloud-based applications, are a popular choice for students, professionals, and casual users alike. However, like any device connected to the internet, Chromebooks are vulnerable to security threats. A Virtual Private Network (VPN) encrypts your internet traffic … Read more