Unlock Seamless Security: Mastering 1Password Chrome Extensions
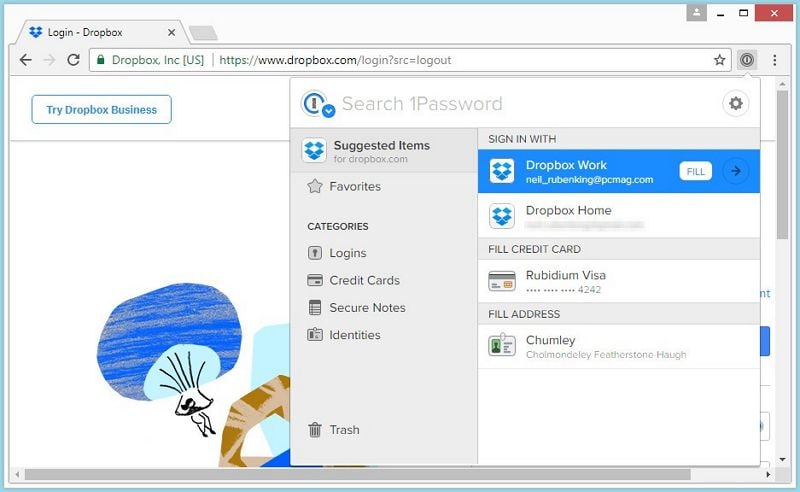
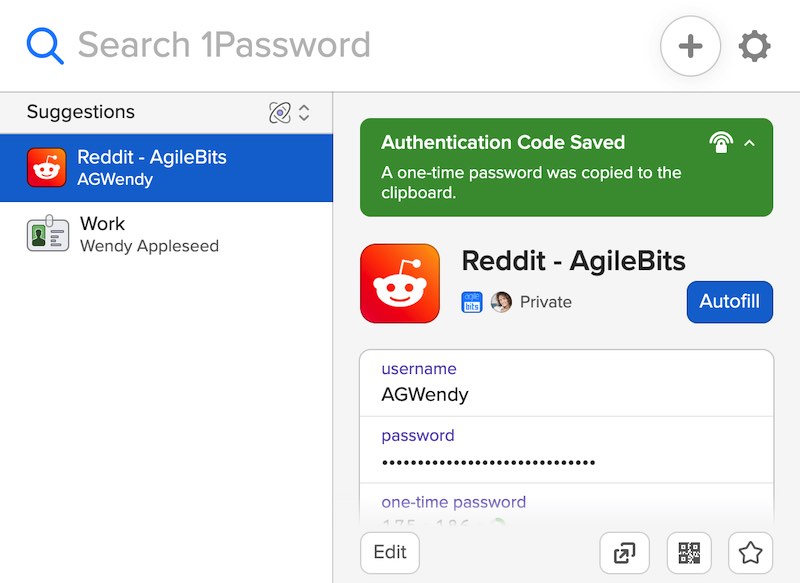
Unlock Seamless Security: Mastering 1Password Chrome Extensions In today’s digital landscape, managing passwords effectively is paramount. The 1Password Chrome extension offers a robust solution for securely storing and automatically filling your credentials, streamlining your online experience and bolstering your cybersecurity posture. This comprehensive guide delves deep into the world of 1Password Chrome extensions, providing you … Read more